This year we have some time problems in the Shellwarp team to participate in the SECCON’s CTF (http://2016.seccon.jp/), only Patatas (team member) and me had some time to check and solve a few of them.
But as we can learn from everything, even the smallest things, here are some writeups from the event.
In this case we get the following statement:
VoIP
Extract a voice.
The flag format is SECCON{[A-Z0-9]}.
voip.pcap
Short and straight to the point. They give us a pcap and the title itself is a huge clue about where we should look. Wireshark has an option to extract VoIP content so, if we are lucky, we may be able to use it to solve the challenge, lets go:
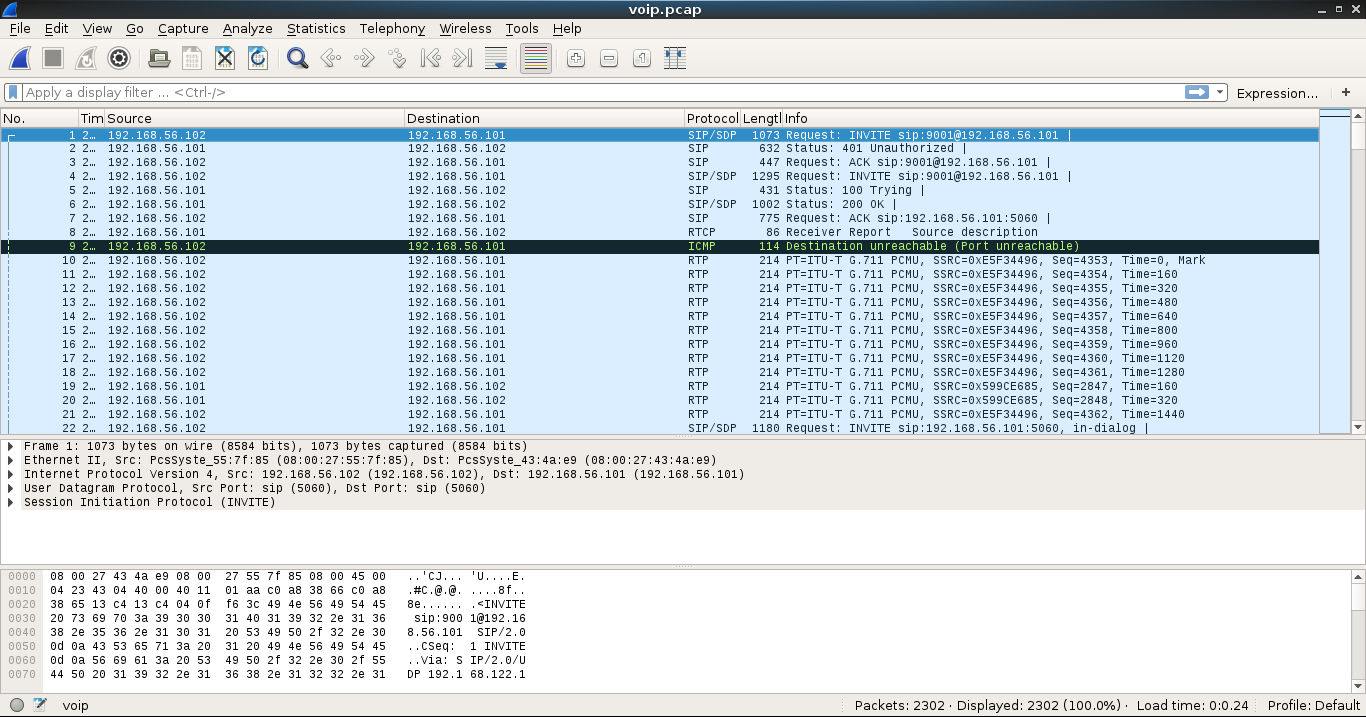
In the top menu click on “Telephony” -> “VoIP Calls” and we get the following window:
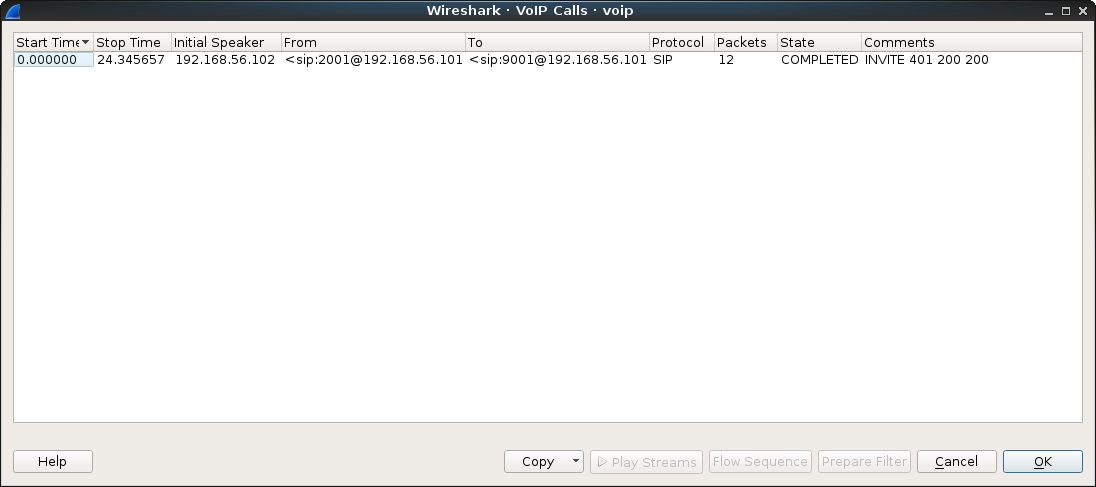
Looks like we got lucky, we select the call and click on “Play streams”:
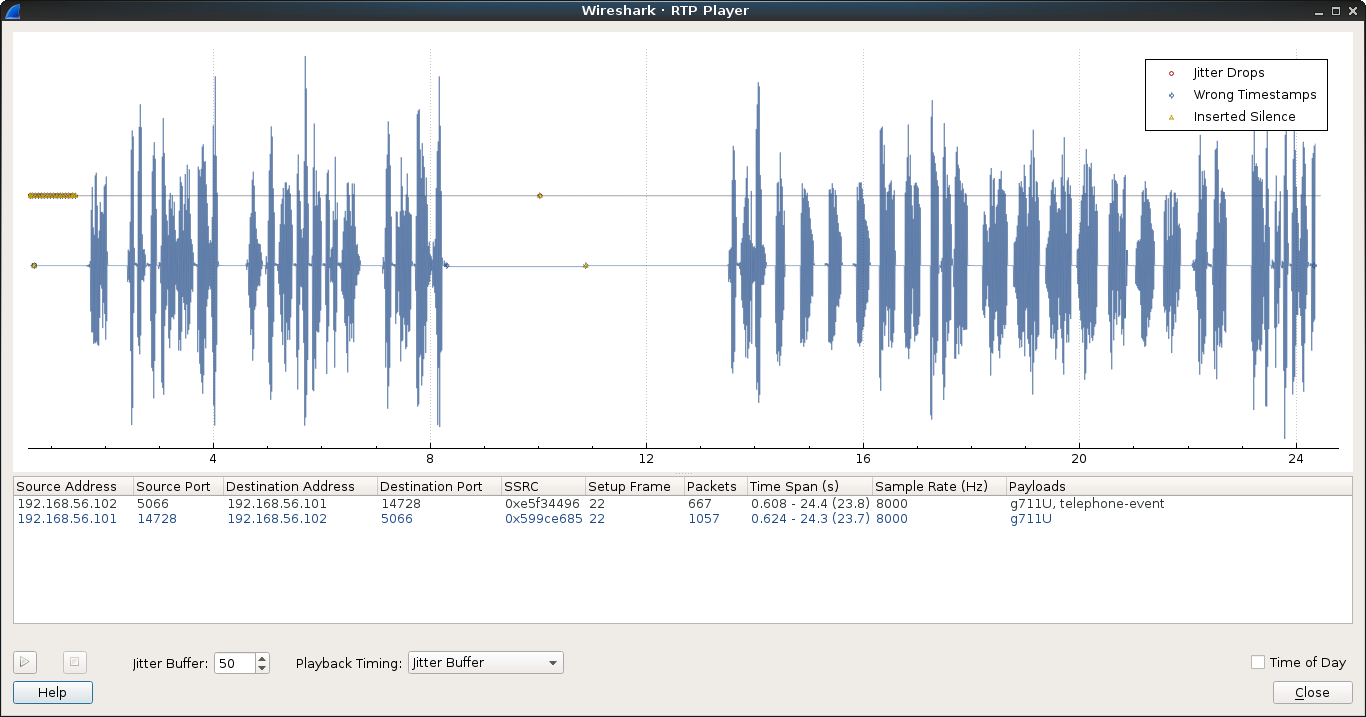
If we click on play we can hear what looks like the SECCON’s voice mail, and at the end it will spell the flag for us, remembering us of the flag format:
SECCON{9001IVR}
I may say that this was one of the easiest ones and most of the teams got it, but it was a nice practice hehe
Regards and thanks for the visit!

