Superando el tercio de pruebas vamos a por la sexta que nos deja el siguiente enunciado y link:
This exercise consists of three files: an executable, an image and an encrypted 7z. Somehow the three files are related. Find out how and validate the flag.
https://s3.eu-central-1.amazonaws.com/cyberrange/cyb_2017_quals/objective6.zip
En este caso nos dan una imagen, un archivo 7z y un binario, como animal de costumbres que soy lo primero que hice fue investigar la imagen a ver si encontraba algo pero después de darle mil vueltas y perder un tiempo valioso decidí irme a por el binario a ver si tenía más suerte, lo cargue en gdb con peda e hice un disas main:
0x56555700 <+0>: lea ecx,[esp+0x4] 0x56555704 <+4>: and esp,0xfffffff0 0x56555707 <+7>: push DWORD PTR [ecx-0x4] 0x5655570a <+10>: push ebp 0x5655570b <+11>: mov ebp,esp 0x5655570d <+13>: push edi 0x5655570e <+14>: push esi 0x5655570f <+15>: push ebx 0x56555710 <+16>: push ecx 0x56555711 <+17>: sub esp,0x878 0x56555717 <+23>: call 0x565555d0 <__x86.get_pc_thunk.bx> 0x5655571c <+28>: add ebx,0x18e4 0x56555722 <+34>: mov esi,ecx 0x56555724 <+36>: mov BYTE PTR [ebp-0x6d],0x41 0x56555728 <+40>: mov BYTE PTR [ebp-0x6c],0x42 0x5655572c <+44>: mov BYTE PTR [ebp-0x6b],0x43 0x56555730 <+48>: mov BYTE PTR [ebp-0x6a],0x44 0x56555734 <+52>: mov BYTE PTR [ebp-0x69],0x45 0x56555738 <+56>: mov BYTE PTR [ebp-0x68],0x46 0x5655573c <+60>: mov BYTE PTR [ebp-0x67],0x47 0x56555740 <+64>: mov BYTE PTR [ebp-0x66],0x48 0x56555744 <+68>: mov BYTE PTR [ebp-0x65],0x49 0x56555748 <+72>: mov BYTE PTR [ebp-0x64],0x4a 0x5655574c <+76>: mov BYTE PTR [ebp-0x63],0x4b 0x56555750 <+80>: mov BYTE PTR [ebp-0x62],0x4c 0x56555754 <+84>: mov BYTE PTR [ebp-0x61],0x4d 0x56555758 <+88>: mov BYTE PTR [ebp-0x60],0x4e 0x5655575c <+92>: mov BYTE PTR [ebp-0x5f],0x4f 0x56555760 <+96>: mov BYTE PTR [ebp-0x5e],0x50 0x56555764 <+100>: mov BYTE PTR [ebp-0x5d],0x51 0x56555768 <+104>: mov BYTE PTR [ebp-0x5c],0x52 0x5655576c <+108>: mov BYTE PTR [ebp-0x5b],0x53 0x56555770 <+112>: mov BYTE PTR [ebp-0x5a],0x54 0x56555774 <+116>: mov BYTE PTR [ebp-0x59],0x55 0x56555778 <+120>: mov BYTE PTR [ebp-0x58],0x56 0x5655577c <+124>: mov BYTE PTR [ebp-0x57],0x57 0x56555780 <+128>: mov BYTE PTR [ebp-0x56],0x58 0x56555784 <+132>: mov BYTE PTR [ebp-0x55],0x59 0x56555788 <+136>: mov BYTE PTR [ebp-0x54],0x5a 0x5655578c <+140>: mov BYTE PTR [ebp-0x53],0x5f 0x56555790 <+144>: mov BYTE PTR [ebp-0x52],0x61 0x56555794 <+148>: mov BYTE PTR [ebp-0x51],0x62 0x56555798 <+152>: mov BYTE PTR [ebp-0x50],0x63 0x5655579c <+156>: mov BYTE PTR [ebp-0x4f],0x64 0x565557a0 <+160>: mov BYTE PTR [ebp-0x4e],0x65 0x565557a4 <+164>: mov BYTE PTR [ebp-0x4d],0x66 0x565557a8 <+168>: mov BYTE PTR [ebp-0x4c],0x67 0x565557ac <+172>: mov BYTE PTR [ebp-0x4b],0x68 0x565557b0 <+176>: mov BYTE PTR [ebp-0x4a],0x69 0x565557b4 <+180>: mov BYTE PTR [ebp-0x49],0x6a 0x565557b8 <+184>: mov BYTE PTR [ebp-0x48],0x6b 0x565557bc <+188>: mov BYTE PTR [ebp-0x47],0x6c 0x565557c0 <+192>: mov BYTE PTR [ebp-0x46],0x6d 0x565557c4 <+196>: mov BYTE PTR [ebp-0x45],0x6e 0x565557c8 <+200>: mov BYTE PTR [ebp-0x44],0x6f 0x565557cc <+204>: mov BYTE PTR [ebp-0x43],0x70 0x565557d0 <+208>: mov BYTE PTR [ebp-0x42],0x71 0x565557d4 <+212>: mov BYTE PTR [ebp-0x41],0x72 0x565557d8 <+216>: mov BYTE PTR [ebp-0x40],0x73 0x565557dc <+220>: mov BYTE PTR [ebp-0x3f],0x74 0x565557e0 <+224>: mov BYTE PTR [ebp-0x3e],0x75 0x565557e4 <+228>: mov BYTE PTR [ebp-0x3d],0x76 0x565557e8 <+232>: mov BYTE PTR [ebp-0x3c],0x77 0x565557ec <+236>: mov BYTE PTR [ebp-0x3b],0x78 0x565557f0 <+240>: mov BYTE PTR [ebp-0x3a],0x79 0x565557f4 <+244>: mov BYTE PTR [ebp-0x39],0x7a 0x565557f8 <+248>: cmp DWORD PTR [esi],0x1 0x565557fb <+251>: je 0x56555807 <main+263> 0x565557fd <+253>: mov eax,0x1 0x56555802 <+258>: jmp 0x56555c55 <main+1365> 0x56555807 <+263>: sub esp,0xc 0x5655580a <+266>: lea eax,[ebx-0x1310] 0x56555810 <+272>: push eax 0x56555811 <+273>: call 0x56555570 <exif_data_new_from_file@plt> 0x56555816 <+278>: add esp,0x10 0x56555819 <+281>: mov DWORD PTR [ebp-0x2c],eax 0x5655581c <+284>: cmp DWORD PTR [ebp-0x2c],0x0 0x56555820 <+288>: jne 0x56555847 <main+327> 0x56555822 <+290>: mov eax,DWORD PTR [esi+0x4] 0x56555825 <+293>: add eax,0x4 0x56555828 <+296>: mov eax,DWORD PTR [eax] 0x5655582a <+298>: sub esp,0x8 0x5655582d <+301>: push eax 0x5655582e <+302>: lea eax,[ebx-0x1304] 0x56555834 <+308>: push eax 0x56555835 <+309>: call 0x56555500 <printf@plt> 0x5655583a <+314>: add esp,0x10 0x5655583d <+317>: mov eax,0x2 0x56555842 <+322>: jmp 0x56555c55 <main+1365> 0x56555847 <+327>: mov DWORD PTR [ebp-0x28],0x0 0x5655584e <+334>: jmp 0x56555b04 <main+1028> 0x56555853 <+339>: cmp DWORD PTR [ebp-0x28],0x0 0x56555857 <+343>: jne 0x5655590a <main+522> 0x5655585d <+349>: lea eax,[ebp-0x881] 0x56555863 <+355>: mov ecx,0x64 0x56555868 <+360>: mov esi,0x0 0x5655586d <+365>: mov DWORD PTR [eax],esi 0x5655586f <+367>: mov DWORD PTR [eax+ecx*1-0x4],esi 0x56555873 <+371>: lea edx,[eax+0x4] 0x56555876 <+374>: and edx,0xfffffffc 0x56555879 <+377>: sub eax,edx 0x5655587b <+379>: add ecx,eax 0x5655587d <+381>: and ecx,0xfffffffc 0x56555880 <+384>: shr ecx,0x2 0x56555883 <+387>: mov edi,edx 0x56555885 <+389>: mov eax,esi 0x56555887 <+391>: rep stos DWORD PTR es:[edi],eax 0x56555889 <+393>: movzx eax,BYTE PTR [ebp-0x5b] 0x5655588d <+397>: mov BYTE PTR [ebp-0x881],al 0x56555893 <+403>: movzx eax,BYTE PTR [ebp-0x44] 0x56555897 <+407>: mov BYTE PTR [ebp-0x880],al 0x5655589d <+413>: movzx eax,BYTE PTR [ebp-0x4d] 0x565558a1 <+417>: mov BYTE PTR [ebp-0x87f],al 0x565558a7 <+423>: movzx eax,BYTE PTR [ebp-0x3f] 0x565558ab <+427>: mov BYTE PTR [ebp-0x87e],al 0x565558b1 <+433>: movzx eax,BYTE PTR [ebp-0x3c] 0x565558b5 <+437>: mov BYTE PTR [ebp-0x87d],al 0x565558bb <+443>: movzx eax,BYTE PTR [ebp-0x52] 0x565558bf <+447>: mov BYTE PTR [ebp-0x87c],al 0x565558c5 <+453>: movzx eax,BYTE PTR [ebp-0x41] 0x565558c9 <+457>: mov BYTE PTR [ebp-0x87b],al 0x565558cf <+463>: movzx eax,BYTE PTR [ebp-0x4e] 0x565558d3 <+467>: mov BYTE PTR [ebp-0x87a],al 0x565558d9 <+473>: sub esp,0xc 0x565558dc <+476>: lea eax,[ebp-0x881] 0x565558e2 <+482>: push eax 0x565558e3 <+483>: call 0x56555560 <exif_tag_from_name@plt> 0x565558e8 <+488>: add esp,0x10 0x565558eb <+491>: mov DWORD PTR [ebp-0x30],eax 0x565558ee <+494>: mov eax,DWORD PTR [ebp-0x2c] 0x565558f1 <+497>: mov eax,DWORD PTR [eax] 0x565558f3 <+499>: sub esp,0x8 0x565558f6 <+502>: push DWORD PTR [ebp-0x30] 0x565558f9 <+505>: push eax 0x565558fa <+506>: call 0x56555550 <exif_content_get_entry@plt> 0x565558ff <+511>: add esp,0x10 0x56555902 <+514>: mov DWORD PTR [ebp-0x24],eax 0x56555905 <+517>: jmp 0x56555b00 <main+1024> 0x5655590a <+522>: cmp DWORD PTR [ebp-0x28],0x1 0x5655590e <+526>: jne 0x56555a11 <main+785> 0x56555914 <+532>: lea eax,[ebp-0x881] 0x5655591a <+538>: mov ecx,0x64 0x5655591f <+543>: mov esi,0x0 0x56555924 <+548>: mov DWORD PTR [eax],esi 0x56555926 <+550>: mov DWORD PTR [eax+ecx*1-0x4],esi 0x5655592a <+554>: lea edx,[eax+0x4] 0x5655592d <+557>: and edx,0xfffffffc 0x56555930 <+560>: sub eax,edx 0x56555932 <+562>: add ecx,eax 0x56555934 <+564>: and ecx,0xfffffffc 0x56555937 <+567>: shr ecx,0x2 0x5655593a <+570>: mov edi,edx 0x5655593c <+572>: mov eax,esi 0x5655593e <+574>: rep stos DWORD PTR es:[edi],eax 0x56555940 <+576>: movzx eax,BYTE PTR [ebp-0x65] 0x56555944 <+580>: mov BYTE PTR [ebp-0x881],al 0x5655594a <+586>: movzx eax,BYTE PTR [ebp-0x46] 0x5655594e <+590>: mov BYTE PTR [ebp-0x880],al 0x56555954 <+596>: movzx eax,BYTE PTR [ebp-0x52] 0x56555958 <+600>: mov BYTE PTR [ebp-0x87f],al 0x5655595e <+606>: movzx eax,BYTE PTR [ebp-0x4c] 0x56555962 <+610>: mov BYTE PTR [ebp-0x87e],al 0x56555968 <+616>: movzx eax,BYTE PTR [ebp-0x4e] 0x5655596c <+620>: mov BYTE PTR [ebp-0x87d],al 0x56555972 <+626>: movzx eax,BYTE PTR [ebp-0x6a] 0x56555976 <+630>: mov BYTE PTR [ebp-0x87c],al 0x5655597c <+636>: movzx eax,BYTE PTR [ebp-0x4e] 0x56555980 <+640>: mov BYTE PTR [ebp-0x87b],al 0x56555986 <+646>: movzx eax,BYTE PTR [ebp-0x40] 0x5655598a <+650>: mov BYTE PTR [ebp-0x87a],al 0x56555990 <+656>: movzx eax,BYTE PTR [ebp-0x50] 0x56555994 <+660>: mov BYTE PTR [ebp-0x879],al 0x5655599a <+666>: movzx eax,BYTE PTR [ebp-0x41] 0x5655599e <+670>: mov BYTE PTR [ebp-0x878],al 0x565559a4 <+676>: movzx eax,BYTE PTR [ebp-0x4a] 0x565559a8 <+680>: mov BYTE PTR [ebp-0x877],al 0x565559ae <+686>: movzx eax,BYTE PTR [ebp-0x43] 0x565559b2 <+690>: mov BYTE PTR [ebp-0x876],al 0x565559b8 <+696>: movzx eax,BYTE PTR [ebp-0x3f] 0x565559bc <+700>: mov BYTE PTR [ebp-0x875],al 0x565559c2 <+706>: movzx eax,BYTE PTR [ebp-0x4a] 0x565559c6 <+710>: mov BYTE PTR [ebp-0x874],al 0x565559cc <+716>: movzx eax,BYTE PTR [ebp-0x44] 0x565559d0 <+720>: mov BYTE PTR [ebp-0x873],al 0x565559d6 <+726>: movzx eax,BYTE PTR [ebp-0x45] 0x565559da <+730>: mov BYTE PTR [ebp-0x872],al 0x565559e0 <+736>: sub esp,0xc 0x565559e3 <+739>: lea eax,[ebp-0x881] 0x565559e9 <+745>: push eax 0x565559ea <+746>: call 0x56555560 <exif_tag_from_name@plt> 0x565559ef <+751>: add esp,0x10 0x565559f2 <+754>: mov DWORD PTR [ebp-0x34],eax 0x565559f5 <+757>: mov eax,DWORD PTR [ebp-0x2c] 0x565559f8 <+760>: mov eax,DWORD PTR [eax] 0x565559fa <+762>: sub esp,0x8 0x565559fd <+765>: push DWORD PTR [ebp-0x34] 0x56555a00 <+768>: push eax 0x56555a01 <+769>: call 0x56555550 <exif_content_get_entry@plt> 0x56555a06 <+774>: add esp,0x10 0x56555a09 <+777>: mov DWORD PTR [ebp-0x20],eax 0x56555a0c <+780>: jmp 0x56555b00 <main+1024> 0x56555a11 <+785>: lea eax,[ebp-0x881] 0x56555a17 <+791>: mov ecx,0x64 0x56555a1c <+796>: mov esi,0x0 0x56555a21 <+801>: mov DWORD PTR [eax],esi 0x56555a23 <+803>: mov DWORD PTR [eax+ecx*1-0x4],esi 0x56555a27 <+807>: lea edx,[eax+0x4] 0x56555a2a <+810>: and edx,0xfffffffc 0x56555a2d <+813>: sub eax,edx 0x56555a2f <+815>: add ecx,eax 0x56555a31 <+817>: and ecx,0xfffffffc 0x56555a34 <+820>: shr ecx,0x2 0x56555a37 <+823>: mov edi,edx 0x56555a39 <+825>: mov eax,esi 0x56555a3b <+827>: rep stos DWORD PTR es:[edi],eax 0x56555a3d <+829>: movzx eax,BYTE PTR [ebp-0x65] 0x56555a41 <+833>: mov BYTE PTR [ebp-0x881],al 0x56555a47 <+839>: movzx eax,BYTE PTR [ebp-0x5b] 0x56555a4b <+843>: mov BYTE PTR [ebp-0x880],al 0x56555a51 <+849>: movzx eax,BYTE PTR [ebp-0x5f] 0x56555a55 <+853>: mov BYTE PTR [ebp-0x87f],al 0x56555a5b <+859>: movzx eax,BYTE PTR [ebp-0x5b] 0x56555a5f <+863>: mov BYTE PTR [ebp-0x87e],al 0x56555a65 <+869>: movzx eax,BYTE PTR [ebp-0x43] 0x56555a69 <+873>: mov BYTE PTR [ebp-0x87d],al 0x56555a6f <+879>: movzx eax,BYTE PTR [ebp-0x4e] 0x56555a73 <+883>: mov BYTE PTR [ebp-0x87c],al 0x56555a79 <+889>: movzx eax,BYTE PTR [ebp-0x4e] 0x56555a7d <+893>: mov BYTE PTR [ebp-0x87b],al 0x56555a83 <+899>: movzx eax,BYTE PTR [ebp-0x4f] 0x56555a87 <+903>: mov BYTE PTR [ebp-0x87a],al 0x56555a8d <+909>: movzx eax,BYTE PTR [ebp-0x5c] 0x56555a91 <+913>: mov BYTE PTR [ebp-0x879],al 0x56555a97 <+919>: movzx eax,BYTE PTR [ebp-0x52] 0x56555a9b <+923>: mov BYTE PTR [ebp-0x878],al 0x56555aa1 <+929>: movzx eax,BYTE PTR [ebp-0x3f] 0x56555aa5 <+933>: mov BYTE PTR [ebp-0x877],al 0x56555aab <+939>: movzx eax,BYTE PTR [ebp-0x4a] 0x56555aaf <+943>: mov BYTE PTR [ebp-0x876],al 0x56555ab5 <+949>: movzx eax,BYTE PTR [ebp-0x45] 0x56555ab9 <+953>: mov BYTE PTR [ebp-0x875],al 0x56555abf <+959>: movzx eax,BYTE PTR [ebp-0x4c] 0x56555ac3 <+963>: mov BYTE PTR [ebp-0x874],al 0x56555ac9 <+969>: movzx eax,BYTE PTR [ebp-0x40] 0x56555acd <+973>: mov BYTE PTR [ebp-0x873],al 0x56555ad3 <+979>: sub esp,0xc 0x56555ad6 <+982>: lea eax,[ebp-0x881] 0x56555adc <+988>: push eax 0x56555add <+989>: call 0x56555560 <exif_tag_from_name@plt> 0x56555ae2 <+994>: add esp,0x10 0x56555ae5 <+997>: mov DWORD PTR [ebp-0x38],eax 0x56555ae8 <+1000>: mov eax,DWORD PTR [ebp-0x2c] 0x56555aeb <+1003>: mov eax,DWORD PTR [eax+0x8] 0x56555aee <+1006>: sub esp,0x8 0x56555af1 <+1009>: push DWORD PTR [ebp-0x38] 0x56555af4 <+1012>: push eax 0x56555af5 <+1013>: call 0x56555550 <exif_content_get_entry@plt> 0x56555afa <+1018>: add esp,0x10 0x56555afd <+1021>: mov DWORD PTR [ebp-0x1c],eax 0x56555b00 <+1024>: add DWORD PTR [ebp-0x28],0x1 0x56555b04 <+1028>: cmp DWORD PTR [ebp-0x28],0x2 0x56555b08 <+1032>: jle 0x56555853 <main+339> 0x56555b0e <+1038>: cmp DWORD PTR [ebp-0x1c],0x0 0x56555b12 <+1042>: je 0x56555bd0 <main+1232> 0x56555b18 <+1048>: cmp DWORD PTR [ebp-0x20],0x0 0x56555b1c <+1052>: je 0x56555bd0 <main+1232> 0x56555b22 <+1058>: cmp DWORD PTR [ebp-0x24],0x0 0x56555b26 <+1062>: je 0x56555bd0 <main+1232> 0x56555b2c <+1068>: sub esp,0x4 0x56555b2f <+1071>: push 0x400 0x56555b34 <+1076>: lea eax,[ebp-0x881] 0x56555b3a <+1082>: push eax 0x56555b3b <+1083>: push DWORD PTR [ebp-0x20] 0x56555b3e <+1086>: call 0x56555510 <exif_entry_get_value@plt> 0x56555b43 <+1091>: add esp,0x10 0x56555b46 <+1094>: movzx eax,BYTE PTR [ebp-0x881] 0x56555b4d <+1101>: test al,al 0x56555b4f <+1103>: je 0x56555bd0 <main+1232> 0x56555b51 <+1105>: sub esp,0x8 0x56555b54 <+1108>: lea eax,[ebp-0x881] 0x56555b5a <+1114>: push eax 0x56555b5b <+1115>: lea eax,[ebp-0x46d] 0x56555b61 <+1121>: push eax 0x56555b62 <+1122>: call 0x56555530 <strcpy@plt> 0x56555b67 <+1127>: add esp,0x10 0x56555b6a <+1130>: sub esp,0x4 0x56555b6d <+1133>: push 0x400 0x56555b72 <+1138>: lea eax,[ebp-0x881] 0x56555b78 <+1144>: push eax 0x56555b79 <+1145>: push DWORD PTR [ebp-0x24] 0x56555b7c <+1148>: call 0x56555510 <exif_entry_get_value@plt> 0x56555b81 <+1153>: add esp,0x10 0x56555b84 <+1156>: sub esp,0x8 0x56555b87 <+1159>: lea eax,[ebp-0x881] 0x56555b8d <+1165>: push eax 0x56555b8e <+1166>: lea eax,[ebp-0x46d] 0x56555b94 <+1172>: push eax 0x56555b95 <+1173>: call 0x56555520 <strcat@plt> 0x56555b9a <+1178>: add esp,0x10 0x56555b9d <+1181>: sub esp,0x4 0x56555ba0 <+1184>: push 0x400 0x56555ba5 <+1189>: lea eax,[ebp-0x881] 0x56555bab <+1195>: push eax 0x56555bac <+1196>: push DWORD PTR [ebp-0x1c] 0x56555baf <+1199>: call 0x56555510 <exif_entry_get_value@plt> 0x56555bb4 <+1204>: add esp,0x10 0x56555bb7 <+1207>: sub esp,0x8 0x56555bba <+1210>: lea eax,[ebp-0x881] 0x56555bc0 <+1216>: push eax 0x56555bc1 <+1217>: lea eax,[ebp-0x46d] 0x56555bc7 <+1223>: push eax 0x56555bc8 <+1224>: call 0x56555520 <strcat@plt> 0x56555bcd <+1229>: add esp,0x10 0x56555bd0 <+1232>: mov DWORD PTR [ebp-0x481],0x0 0x56555bda <+1242>: mov DWORD PTR [ebp-0x47d],0x0 0x56555be4 <+1252>: mov DWORD PTR [ebp-0x479],0x0 0x56555bee <+1262>: mov DWORD PTR [ebp-0x475],0x0 0x56555bf8 <+1272>: mov DWORD PTR [ebp-0x471],0x0 0x56555c02 <+1282>: movzx eax,BYTE PTR [ebp-0x468] 0x56555c09 <+1289>: mov BYTE PTR [ebp-0x481],al 0x56555c0f <+1295>: movzx eax,BYTE PTR [ebp-0x465] 0x56555c16 <+1302>: mov BYTE PTR [ebp-0x480],al 0x56555c1c <+1308>: movzx eax,BYTE PTR [ebp-0x467] 0x56555c23 <+1315>: mov BYTE PTR [ebp-0x47f],al 0x56555c29 <+1321>: movzx eax,BYTE PTR [ebp-0x46d] 0x56555c30 <+1328>: mov BYTE PTR [ebp-0x47e],al 0x56555c36 <+1334>: movzx eax,BYTE PTR [ebp-0x462] 0x56555c3d <+1341>: mov BYTE PTR [ebp-0x47d],al 0x56555c43 <+1347>: movzx eax,BYTE PTR [ebp-0x46c] 0x56555c4a <+1354>: mov BYTE PTR [ebp-0x47c],al 0x56555c50 <+1360>: mov eax,0x0 0x56555c55 <+1365>: lea esp,[ebp-0x10] 0x56555c58 <+1368>: pop ecx 0x56555c59 <+1369>: pop ebx 0x56555c5a <+1370>: pop esi 0x56555c5b <+1371>: pop edi 0x56555c5c <+1372>: pop ebp 0x56555c5d <+1373>: lea esp,[ecx-0x4] 0x56555c60 <+1376>: ret
WOW! Como sabéis lo mio no es reversing precisamente así que me impresiono bastante ver todas estas lineas, de buenas a primeras lo que más me llamo la atención fue la llamada a strcat en la dirección 0x56555bc8 así que puse un breakpoint ahí:
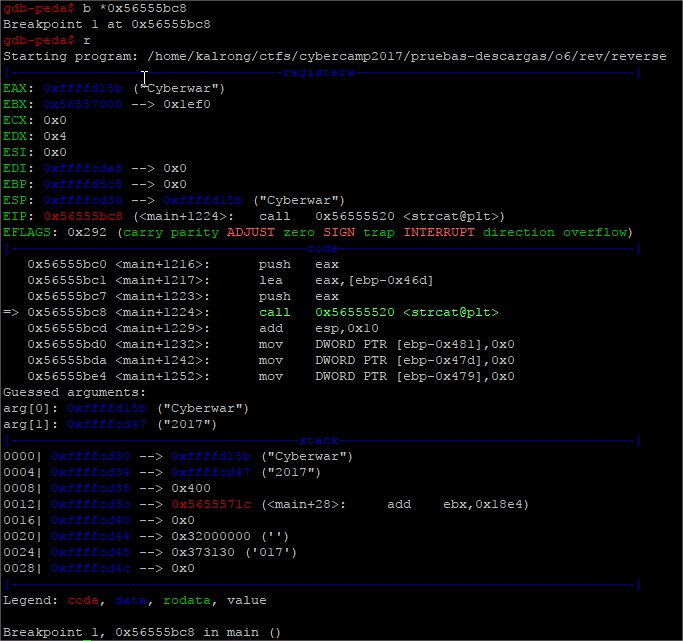
¡Bien he encontrado algo, seguro que es la contraseña del 7z!… Ah pues no… jo
Y es que en mis ansías no me fijé en que a continuación se seguían realizando operaciones, así que una docena de breakpoints después (insisto, reversing no es lo mio probablemente haya mil maneras más faciles de sacarlo jeje) para ir viendo la última parte de la ejecución fui viendo que iba pasando en cada paso. Luego de un par de ejecuciones me fije en que en el registro EAX iban apareciendo una serie de caracteres antes de finalizar la ejecución:
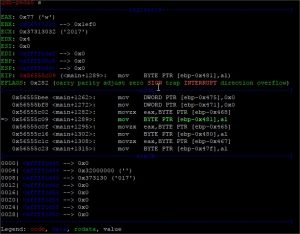
Después de anotarlos me quede con el string w2aC7y, esta vez si que hubo suerte y esta era la contraseña que buscabamos para el 7z, descomprimimos y obtenemos un txt con la flag:
FLAG: ReversingIsCool
Seguramente alguien más ducho en reversing os podría explicar con más detalle que se va haciendo en cada paso y probablemente lo hubiese visto en el primer vistazo, por desgracia reversing es un tema que tengo muy verde y contento me quedo con haberlo conseguido sacar jeje
Un saludo y gracias por vuestra visita!

